Understanding Spear Phishing: A Targeted Cyber Threat
Spear phishing is a specific and more targeted type of phishing attack, which itself is a broad category of cybercrimes. Phishing involves the use of deceptive emails, text messages, or phone calls to manipulate individuals into revealing sensitive information such as credit card numbers, social security details, or login credentials. These attacks can also trick victims into downloading malware, visiting malicious websites, or transferring money to fraudulent recipients. Phishing is a common attack method, with the FBI receiving over 300,000 phishing complaints in 2022 alone.
The Difference Between Phishing and Spear Phishing
Phishing attacks are often broad and impersonal. These attacks typically come in the form of mass messages that appear to be from reputable organizations, like well-known companies or global brands, and are sent to thousands or millions of individuals in the hope that some will fall for the scam.
On the other hand, spear phishing is a highly targeted form of phishing. Instead of being sent to large groups, spear phishing messages are carefully crafted for specific individuals or small groups, based on extensive research. The messages are personalized, making them appear to come from trusted sources such as a coworker, manager, or business partner. While spear phishing attacks are less frequent than generic phishing attacks, they are more damaging when successful. According to Barracuda, while spear phishing accounted for just 0.1% of all emails in a given year, these attacks were responsible for 66% of all data breaches.
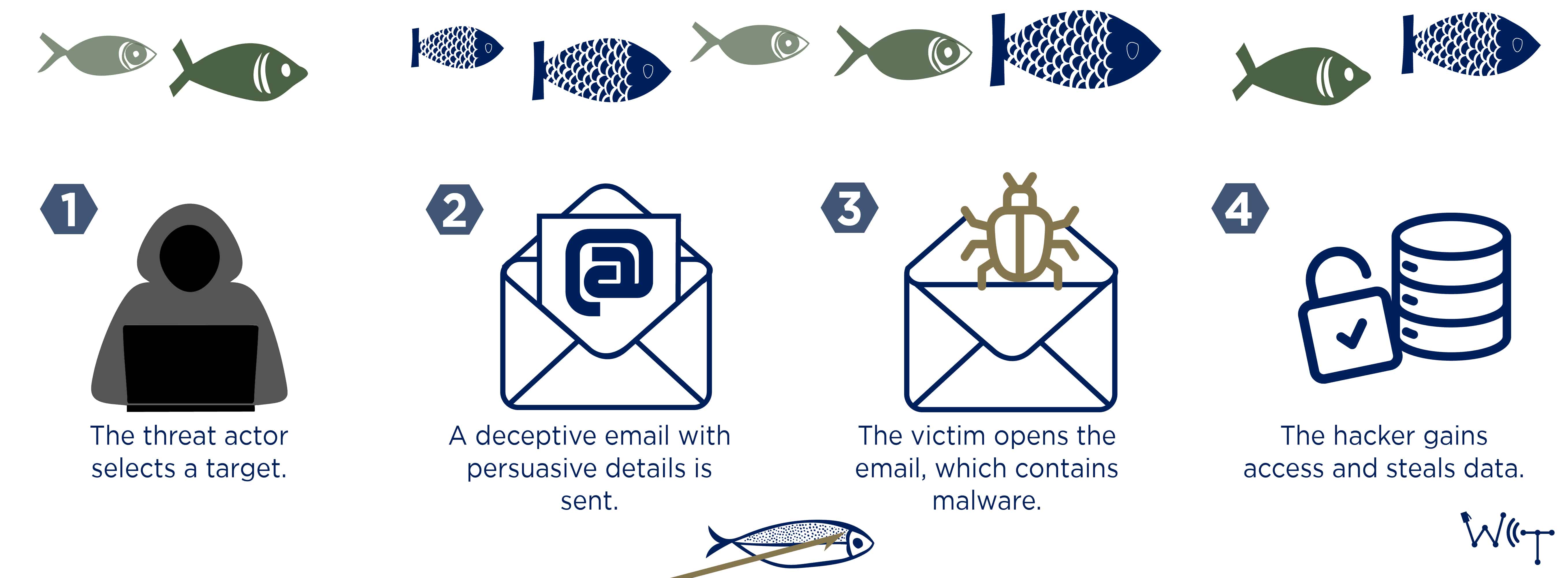
How Spear Phishing Works
Spear phishing attacks are more convincing and harder to spot than traditional phishing for several reasons:
- In-depth Research and Credibility: Spear phishers invest time in researching their targets and crafting believable messages. They often gather information from social media platforms like LinkedIn, or even through hacked company accounts, to learn about the target’s role, job responsibilities, and the vendors or colleagues they interact with. This allows the attacker to create realistic scenarios that appear credible to the victim.
- Social Engineering Tactics: Spear phishing relies heavily on psychological manipulation. Attackers create a sense of urgency or exploit existing relationships to trick the target into making rash decisions. For instance, they might pose as a colleague and urgently request funds or sensitive data. Some even go so far as to ask victims to keep the transaction confidential, furthering the illusion of legitimacy.
- Multiple Message Types: Modern spear phishing campaigns often use multiple communication channels to build trust. For example, they might include phone numbers or links to fake websites, which the target can follow to "confirm" the authenticity of the request. Some attacks even employ smishing (text-based phishing) or vishing (voice phishing) in addition to email-based spear phishing.
Common Types of Spear Phishing
Spear phishing attacks can be further categorized based on their targets and methods:
- Business Email Compromise (BEC): This is a common form of spear phishing targeting businesses. Cybercriminals impersonate employees, managers, or trusted partners to trick others within the organization into transferring money, sending confidential data, or even opening malware-laden attachments. In more advanced cases, attackers may hijack email accounts to make their scams appear even more legitimate.
- CEO Fraud: A specialized form of BEC, CEO fraud involves scammers impersonating high-ranking executives, pressuring lower-level employees to wire large sums of money or share sensitive information.
- Whale Phishing: This type of spear phishing targets high-profile individuals—referred to as "whales"—such as C-level executives, board members, or public figures like celebrities and politicians. Whale phishing requires even more detailed research and is focused on exploiting the high-value information or assets these individuals hold.
Real-World Example of Spear Phishing
A notable example of spear phishing occurred in August 2022, when Twilio, a cloud-based communications company, fell victim to an elaborate attack. Hackers impersonated Twilio’s IT department by sending fake SMS messages claiming that employees needed to reset their passwords or update their schedules. The messages directed victims to a fake website that harvested their login credentials. The attackers then used these credentials to breach Twilio’s corporate network, impacting over 163 of its client organizations, including the encrypted messaging app Signal. The Twilio case highlights the increasing sophistication and danger of spear phishing attacks.
Protecting Against Spear Phishing
Preventing spear phishing attacks requires multiple layers of defense. Essential tools include email security systems, antivirus software, and multi-factor authentication (MFA), which add an additional layer of protection against unauthorized access. However, the human element remains a critical part of the defense. Many organizations are investing in security awareness training and simulated phishing campaigns to educate employees about the risks and warning signs of phishing.
In addition, real-time threat detection and response like Endpoint Detection and Response (EDR) capabilities are crucial for identifying and mitigating attacks swiftly. With these strategies in place, businesses can better safeguard themselves against spear phishing and other cyber threats.
Spear phishing is a highly targeted and increasingly common form of cyberattack that uses careful research and social engineering to exploit personal and professional relationships. By understanding the tactics behind spear phishing and implementing robust security measures, organizations and individuals can better protect themselves from these dangerous and costly attacks.
Protect your team from the ever-evolving threats of spear phishing with our expert IT solutions. Want to safeguard your business from spear phishing attacks? Our expert IT solutions can help you stay ahead of cybercriminals. Let’s build a strong defense – contact us today!

