
You've Been Breached, Now What?
“Dear Client, we regret to notify you that one of the several records that our organization recently had a data breach included your personal information.”
No one wants to hear these words. Knowing that your personal information is now in the hands of cybercriminals or being used against the businesses you trust is unsettling. If you are a business owner, the breach might involve third-party vendors or partners, further eroding trust and patience.
Stay Calm, It Happens More Than You Think
Whether you are a consumer or a business owner, take a moment to breathe.
Data breaches have become increasingly common. The Identity Theft Resource Center reported a 77% increase in data compromises in 2023 compared to 2022. On July 4, 2024 10 billion passwords have been posted to hacking sites. These unique plaintext passwords were likely the largest password compilation to date, calling it “10 billion RockYou2024 Password Compilation”. Major corporations, banks, and even government agencies have fallen victim to these breaches. While unsettling, understanding that you are not alone can help alleviate some stress.
Stay calm and know that you have rights as both a consumer and a business owner.
Check the Breach Details and Stay Informed
Once you receive that dreaded notification, don't ignore it.
Examine the specifics provided by the affected company. Understand what type of information has been compromised—whether it's personal details, login credentials, or sensitive data like financial information. This knowledge is crucial for taking actions to minimize risks.
Staying informed empowers you to protect yourself and your business. Companies are legally required to disclose breach details, so read the information carefully.
Change Passwords and Enable Multi-Factor Authentication
In 2023, the most common password worldwide was "123456," used over 4.5 million times, followed by "admin," and other weak combinations. An ideal password should have 12 characters, combining letters, numbers, and symbols. Nonetheless, certain websites may not accommodate special characters or may have restrictions on password length.
The following chart shows the time difference in which brute force attacks crack your password and how adding complexity and lengthening your passwords drastically increases the time required:
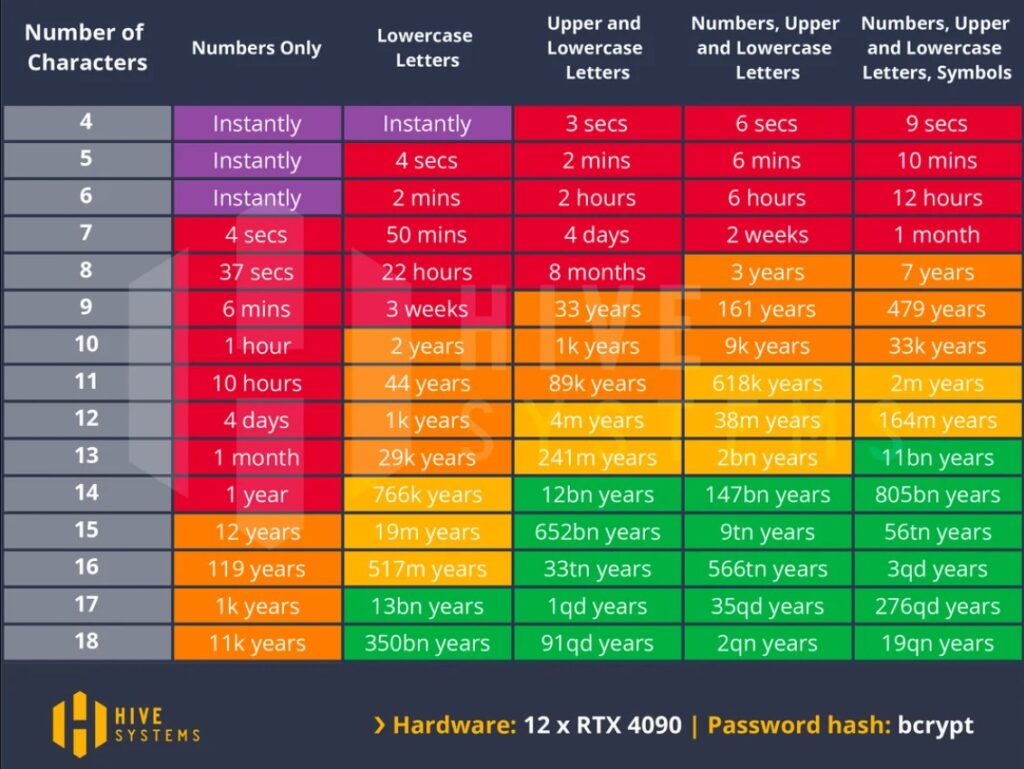
Cybercriminals exploit weak passwords to gain unauthorized access. Change your passwords for the breached account and any other accounts where you use similar passwords. Enable Multi-Factor Authentication (MFA) wherever possible to add an extra layer of security, requiring a second form of verification.
Monitor Your Financial Statements
Keep a close eye on your financial and online accounts for any unusual activity. Regularly review bank statements, credit card transactions, and other financial accounts for signs of suspicious activity. Report any anomalies, no matter how small, to your financial institution immediately. Most institutions have robust fraud protection measures and can guide you through securing your accounts.
Notify Relevant Parties
Inform necessary parties about the breach to prevent further damage. Contact your bank or financial institution to alert them of potential fraud. Notify the affected service providers or websites where the breach occurred. Report the breach to your employer if it involves work-related accounts or data.
Secure Your Devices
Ensure that your devices are secure to prevent future breaches. Update your operating system and software to the latest versions to patch any vulnerabilities. If the breach is severe or you are unsure of the extent of the damage, seek professional assistance. Contact our team of cybersecurity experts to conduct a thorough investigation and assist with mitigation.
Whether you're a consumer or a business owner, a data breach can be troubling. However, you're not powerless. Stay informed, take proactive steps to secure your accounts, and leverage your rights.
Contact West Central Technology to learn more about protecting against, preparing for, and responding to data breaches.
